Reverse Engineering Serial over USB
Abhijit, 21 August 2022
I recently discovered that the GWInstek power supply (GPD-3303D) had a USB-B connector on the back - which meant it could have some remote monitoring and control features. Sure enough, the user manual lists all the serial commands and also has a dedicated windows executable with a GUI for sending the commands. Unfortunately, when I tried to replicate the commands through minicom, it did not work, leading me down a rabbit-hole of USB/serial debugging.

First I wanted to check if the serial settings (Port number, baud rate, number of bits etc.) were all correct.
First off, with the power supply connected over USB, it showed up in lsusb as a native FT232 device with the expected /dev/ttyUSB0 serial port - meaning that a standard serial interface should work. Also, with Minicom configured as per the manual, powering up the 3303D printed out some standard text about a firmware update - confirming that the settings were also correct. (9600 baud with 1 stop bit, no parity, no flow control). The 3303D has no echo mode - so there is no feedback about whether the device is actually getting any bytes sent to it.
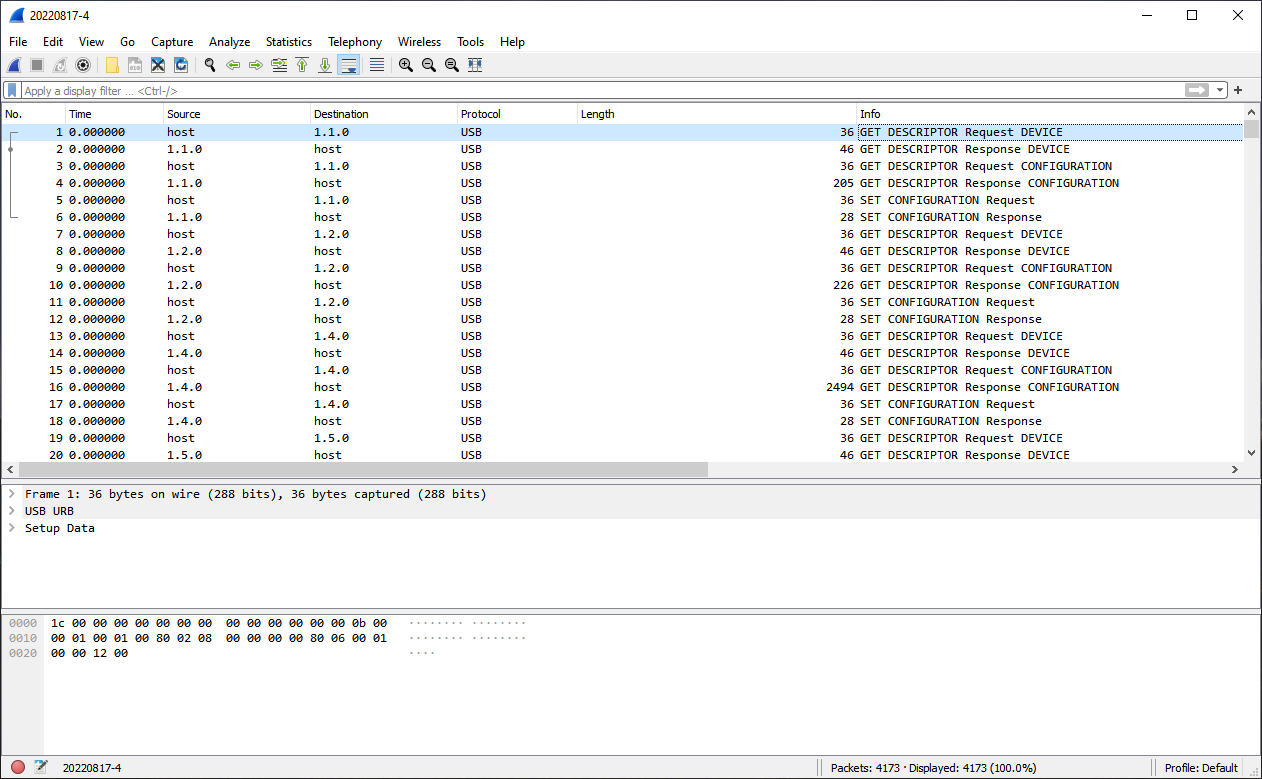
I decided to check with the manufacturer’s software, fortunately I had a Windows machine, and that worked. That meant that the problem could be either with the byte sequences, or end-of-line sequence (CR/LF/CRLF), or something else entirely. To figure out what byte sequences were working, I installed USBpcap and Wireshark; and got a dump of the USB transactions as shown here. Since the data is being sent to the USB, it has more data than just the bytes to be sent on serial.
All USB Data (contains data for all devices - incuding a USB keyboard, mouse etc)
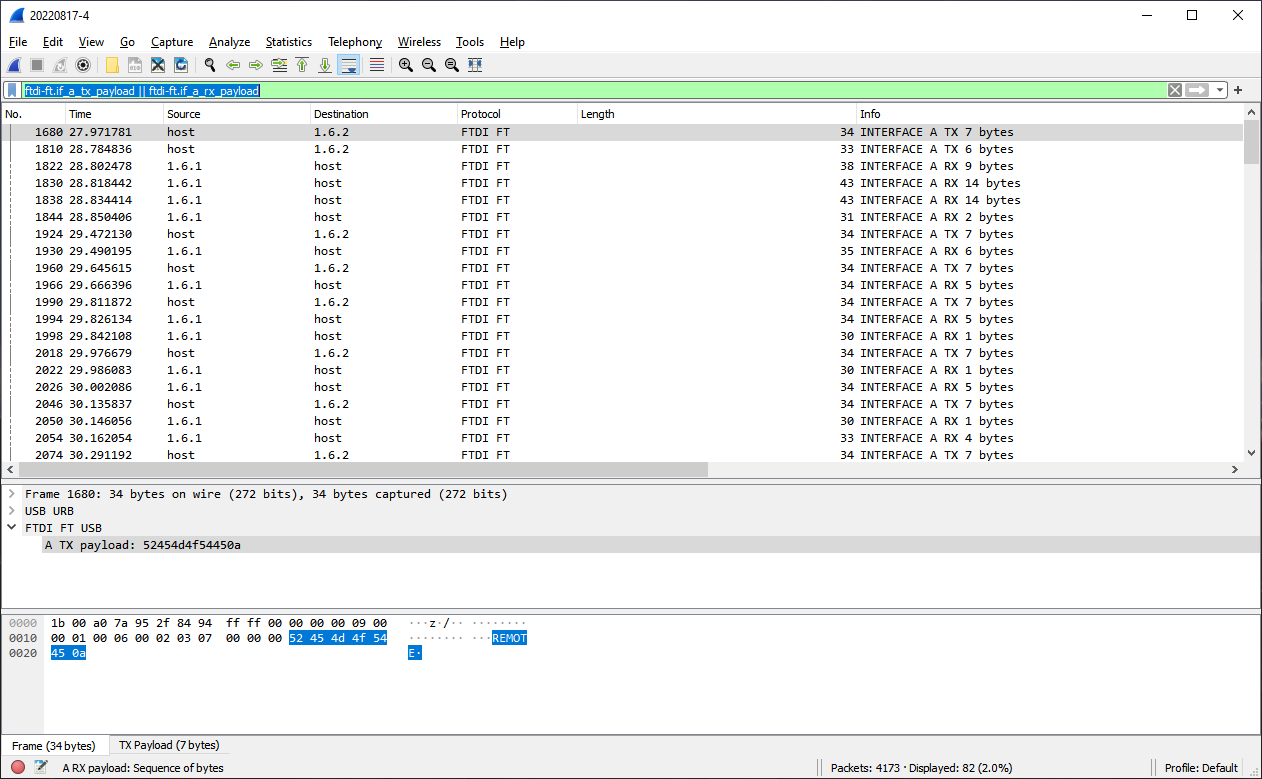
Filtered packets showing only FTDI Data
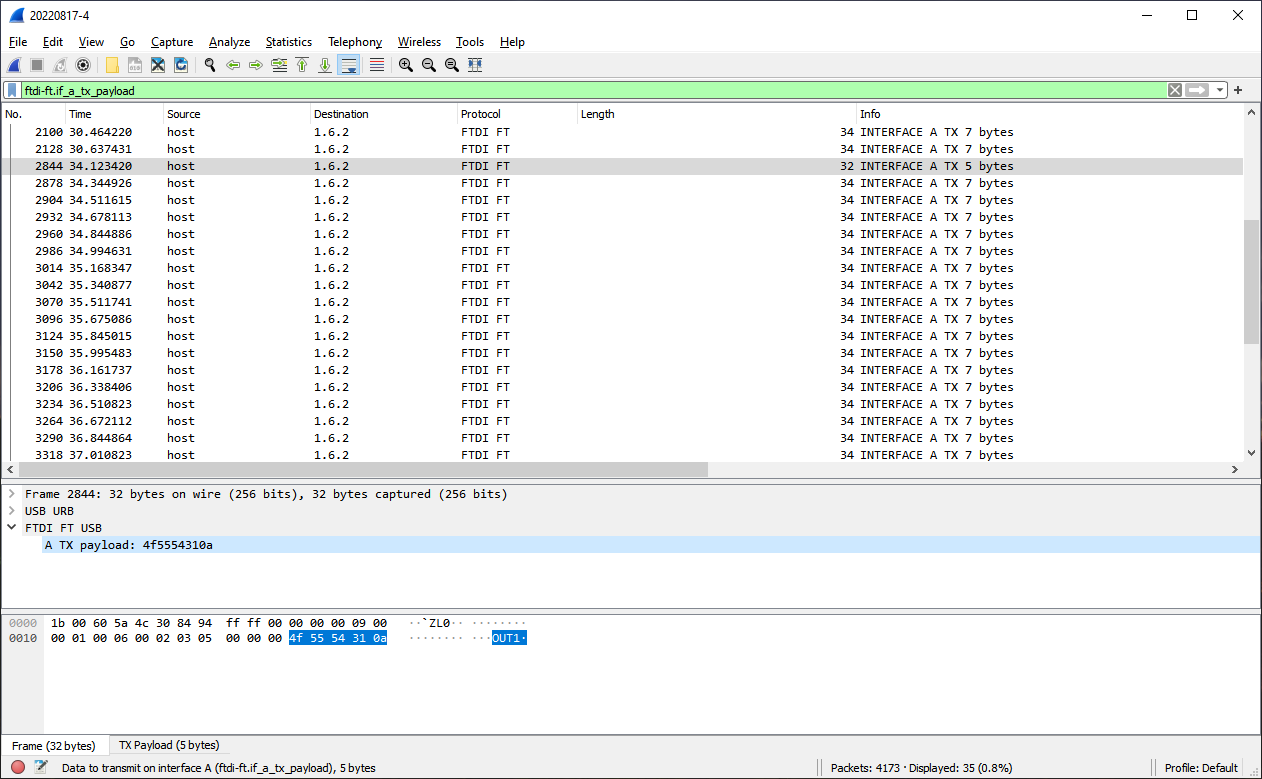
Filtered packets showing only FTDI Transmit Data (TX)
And that clearly shows us:
- The commands are:
REMOTE(to start the remote session);OUT0andOUT1to control the output; etc. - Moreover, the end-of-line character is a linefeed (
0x0a). - The software periodically ‘talks’ on the USB interface to keep the connection ‘alive’. If you don’t do this you need to start each new set of commands with
REMOTE.
NOTES:
- Docklite (Windows only) is a great tool for debugging serial - although the free version has some annoying limitations
- There is a python library as well but I was not able to get it to work and did not have time to debug.